
Research
Security News
Malicious npm Package Typosquats react-login-page to Deploy Keylogger
Socket researchers unpack a typosquatting package with malicious code that logs keystrokes and exfiltrates sensitive data to a remote server.
@aws-cdk/aws-iam
Advanced tools
Changelog
0.29.0 (2019-04-24)
app.run() (#2300) (47ff448), closes #2289 awslabs/jsii#456Code, CfnParametersCode. (#2027) (4247966)MetricCustomization to MetricOptions.outputArtifact and outputArtifacts properties.inputArtifact(s) and additionalInputArtifacts properties were renamed to input(s) and extraInputs.outputArtifactName(s) and additionalOutputArtifactNames properties were renamed to output(s) and extraOutputs.CodeBuildBuildAction and CodeBuildTestAction were merged into one class CodeBuildAction.JenkinsBuildAction and JenkinsTestAction were merged into one class JenkinsAction.lambda.Function no longer implements IEventRuleTarget. Instead, use @aws-cdk/aws-events-targets.LambdaFunction.sns.Topic no longer implements IEventRuleTarget. Use @aws-cdk/aws-events-targets.SnsTopic instead.codebuild.Project no longer implements IEventRuleTarget. Use @aws-cdk/aws-events-targets.CodeBuildProject.cdk.Root construct has been removed. Use cdk.App instead.stepfunctions.WaitProps: the props seconds, timestamp, secondsPath and timestampPath are now duration of a union-like class WaitDuration (e.g. duration: WaitDuration.seconds(n))codedeploy.ServerDeploymentConfigProps: the props minHealthyHostCount and minHealthyHostPercentage are now minimumHealthyHosts of union-like class MinimumHealthyHosts (e.g. minimumHealthyHosts: MinimumHealthyHosts.percentage(50))cloudformation.CustomResourceProps: the props topicProvider and lambdaProvider are now provider of union-like class CustomResourceProvider (e.g. CustomResourceProvider.lambda(fn)cloudformation.CustomResource no longer extends CfnCustomResource.ssm.ParameterProps renamed to ssm.ParameterOptions.aws-ec2.InstanceSize.None was renamed to InstanceSize.Nanovpc.selectSubnetIds(...) has been replaced with vpc.selectSubnets(...).subnetIds.Readme
Define a role and add permissions to it. This will automatically create and attach an IAM policy to the role:
Define a policy and attach it to groups, users and roles. Note that it is possible to attach
the policy either by calling xxx.attachInlinePolicy(policy) or policy.attachToXxx(xxx).
attaching policies to user and group
Managed policies can be attached using xxx.attachManagedPolicy(arn):
If you need to create roles that will be assumed by 3rd parties, it is generally a good idea to require an ExternalId
to assume them. Configuring
an ExternalId works like this:
When we say Principal, we mean an entity you grant permissions to. This
entity can be an AWS Service, a Role, or something more abstract such as "all
users in this account" or even "all users in this organization". An
Identity is an IAM representing a single IAM entity that can have
a policy attached, one of Role, User, or Group.
When defining policy statements as part of an AssumeRole policy or as part of a
resource policy, statements would usually refer to a specific IAM principal
under Principal.
IAM principals are modeled as classes that derive from the iam.PolicyPrincipal
abstract class. Principal objects include principal type (string) and value
(array of string), optional set of conditions and the action that this principal
requires when it is used in an assume role policy document.
To add a principal to a policy statement you can either use the abstract
statement.addPrincipal, one of the concrete addXxxPrincipal methods:
addAwsPrincipal, addArnPrincipal or new ArnPrincipal(arn) for { "AWS": arn }addAwsAccountPrincipal or new AccountPrincipal(accountId) for { "AWS": account-arn }addServicePrincipal or new ServicePrincipal(service) for { "Service": service }addAccountRootPrincipal or new AccountRootPrincipal() for { "AWS": { "Ref: "AWS::AccountId" } }addCanonicalUserPrincipal or new CanonicalUserPrincipal(id) for { "CanonicalUser": id }addFederatedPrincipal or new FederatedPrincipal(federated, conditions, assumeAction) for
{ "Federated": arn } and a set of optional conditions and the assume role action to use.addAnyPrincipal or new AnyPrincipal for { "AWS": "*" }If multiple principals are added to the policy statement, they will be merged together:
const statement = new PolicyStatement();
statement.addServicePrincipal('cloudwatch.amazonaws.com');
statement.addServicePrincipal('ec2.amazonaws.com');
statement.addAwsPrincipal('arn:aws:boom:boom');
Will result in:
{
"Principal": {
"Service": [ "cloudwatch.amazonaws.com", "ec2.amazonaws.com" ],
"AWS": "arn:aws:boom:boom"
}
}
The CompositePrincipal class can also be used to define complex principals, for example:
const role = new iam.Role(this, 'MyRole', {
assumedBy: new iam.CompositePrincipal(
new iam.ServicePrincipal('ec2.amazonawas.com'),
new iam.AccountPrincipal('1818188181818187272')
)
});
FAQs
Unknown package
The npm package @aws-cdk/aws-iam receives a total of 130,696 weekly downloads. As such, @aws-cdk/aws-iam popularity was classified as popular.
We found that @aws-cdk/aws-iam demonstrated a not healthy version release cadence and project activity because the last version was released a year ago. It has 4 open source maintainers collaborating on the project.
Did you know?

Socket for GitHub automatically highlights issues in each pull request and monitors the health of all your open source dependencies. Discover the contents of your packages and block harmful activity before you install or update your dependencies.

Research
Security News
Socket researchers unpack a typosquatting package with malicious code that logs keystrokes and exfiltrates sensitive data to a remote server.
Security News
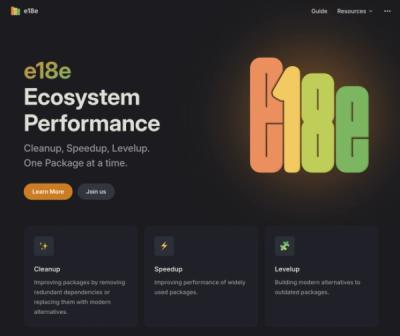
The JavaScript community has launched the e18e initiative to improve ecosystem performance by cleaning up dependency trees, speeding up critical parts of the ecosystem, and documenting lighter alternatives to established tools.
Product
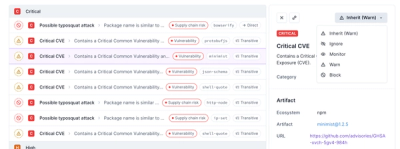
Socket now supports four distinct alert actions instead of the previous two, and alert triaging allows users to override the actions taken for all individual alerts.